System assurors are responsible for their system’s confidentiality, integrity and accessibility. That means back ups. That means back ups of the back ups. That means ensuring your email server is patched and up to date and and unnecessary temporary files are purged to enable an expedient caching and ensure the flawless reception and delivery of emails. With your Pop3 email server under your control, you know exactly when to safely do server restarts and updates, and which updates to skip to prevent sub optimal performance.
But what about when you can’t? Eventually, the scaling cost of expanding your email server, file server, or web hosting server becomes too costly, and outsourcing becomes the only option. Cloud based computing can be very attractive for a system’s administrator. By offsetting the responsibilities of the fallibility of hardware, the inconvenience of off site backups, and the responsibility for appropriately configuring updates, an administrator could mistakenly assume that his organizations information will remain confidential, reliable, and accessible.
Until he realizes that “The Cloud” is just someone else’s computer. A basic tenant of risk management, whether online or in real life is don’t trust what you can’t see. Anything that can go wrong on your personal email server is apt to go wrong on a cloud based service, be it IasS, PaaS, or SaaS. It is a common misconception that by outsourcing a particular function of your network or system, an administrator can relinquish the accountability for the quality of service. Yet when the email system is down, the administrator will undoubtedly answer for it. Therefore it is imperative to utilize the Risk Management framework in any system, be it local, remote, owned, or rented, for the duration of the system development life cycle, otherwise your responsibility as a system assuror is incomplete.
Cloud bases services, counter intuitively, are more vulnerable to break in than your private solution. Your information is being stored in mass in a known, public repository. Bad actors and malicious hackers know your information is being kept by an impartial third party. If your company is attacked, you can almost always assume it was a targeted and deliberate attack, but when bad actors are trying to prise information from Amazon or Google’s databases, they are indiscriminately lashing out at any open port in the cyber storm. Furthermore, due to the aforementioned, herd-like nature of this particular repository, any other organization’s vulnerability, including the organization hosting the cloud based service, could quickly become you own.
By now you may be wondering more about these services. IaaS or Infrastructure as a Service, is merely renting blank server space from a data farm, and configuring the web server, or email host as your own. IaaS is useful for running cloud based file servers, or for offshoring some serious processing like compiling code, churning databases, or rendering graphics in an environment that you create from the ground up. However, some administrators don’t have the ability or the inclination to set up their offsite server rig. Use PaaS if you don’t want to install your own operating system and environment or off site file service, and just need a Platform as a Service from which to operate upon. Naturally, by relinquishing further options in configuration, you are increasing the chance of future vulnerability. The third more common cloud based service is SaaS. A good example of Software as a Service, is the latest iteration of Adobe Photoshop, where you must provide a subscription to use their services, and they keep a copy of your work offsite. Incredibly useful in some ways, incredibly annoying in others, some niche markets require you use the cloud based subscription model of their program. If you are beholden to one such service, all that can be done is comply with the standards provided by the SaaS service, and stick to the Risk Management Framework.
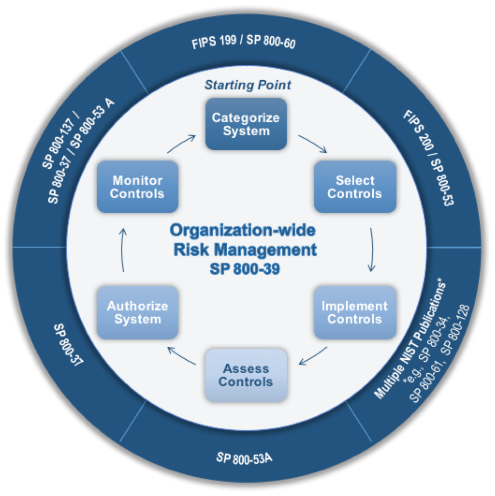
The Risk Management Framework is a continuous six step cadence that helps to ensure your organization’s system remains reliable and secure for the duration of the system’s development life cycle. The procedure is spelled out by many guidelines by the National Institute for Standards in Technology, and most companies adhere to the standardized risk management framework, once the information leaves your hands, you are only operating in good faith, and hoping that nothing goes wrong. And of course things go wrong. In March of 2009, Microsoft, the biggest name in technology at that time, suffered an outage leaving millions with out service. With this in mind, you should always incorporate your cloud based services into your RMF, even when the providers of the service assure you than adhere to NIST standards.
The first step in the RMF, is to categorize the function of the system, and the information that comes into, is kept upon, or leaves that piece of hardware. This information should be rated based upon the impact of that particular piece of information. For example, an inter office chain letter may not be as impactful to the financial security of an organization as a copy of the organizations financial records, so it is important that particular emails and other files are regarded as more or less critical than others, and ensure no indemnifying information is ever stored off site.
The next step after categorization is to select the set of controls you want your organization to adhere to to minimize potential vulnerabilities and access point to your organization from this cloud based service. Unfortunately, the administrator would be facing vendor lock in, as most vendors call the shots on their services, and the details and the minutia could be kept from the organization’s security controller. Therefore, the administrator must carefully select which vendor they believe to be the most thorough and reputable.
Third, Implement. Arguably the most direct step in the Risk Management Framework, implementation is how the system is deployed. For this step in assuring your systems integrity, the administrator must refer to the Service Level Agreement. Assuming your vendor adheres to NIST’s publications, you can assume your information is being kept at an industry level of integrity. As this stage is almost entirely out your hands, it could be considered one of the weaker steps of the cloud based RMF.
After your system is installed, the fourth step of the RMF is to assess the controls and ensure that everything works as intended. From a functional standpoint, this should be simple enough with a cloud based service, but from a practical standpoint, even if you have full control of your systems installation, update, and integration, there are still unknown factors on the vendor’s side of the curtain that you are forced to take for granted.
Once the system is appropriately installed and configured, the next step is to authorize the system’s operation, delegating user levels appropriate to the tasks given them. When appropriate, the use of multi-factor authentication will alleviate many of the concerns to confidentiality a system owner my express at the thought of indemnifying information being kept off site.
And finally, by monitoring the system, the data, and the controls on an ongoing basis through deep packet inspection, and by documenting every major change and update to the system in duplicate, an administrator can ensure due diligence in regard to the final step of the Risk Management Framework, and combat the increased complexity of adhering to NIST recommendations when applying the Risk Management Framework to cloud based services.
Bibliography
SaaS Security Best Practices: Minimizing Risk in the Cloud – (2015)
https://www.intel.com/content/dam/www/public/us/en/documents/white-papers/saas-security-best-practices-minimizing-risk-in-the-cloud-paper.pdf
Cloud - Top 5 Risks with Paas – OWASP (2009)
https://www.owasp.org/index.php/Cloud_-_Top_5_Risks_with_PAAS
Advantages and Disadvantages Of Cloud Computing – Cloud Computing Pros and Cons (2013)
Ilias Tsagklis - https://www.javacodegeeks.com/2013/04/advantages-and-disadvantages-of-cloud-computing-cloud-computing-pros-and-cons.html
